The Chaos Computer Club also know as CCC is the largest association of hackers in Europe. For over 30 years they provide information about technical and societal issues, such as surveillance, privacy, freedom of information, hacktivism, data security and many other interesting things around technology and hacking issues. Every year they organize an event in …
Read More “Let’s discussed the past event of the CCC in Germany”
A serious weakness has been found on CPU and the way they manage information, allowing software to steal information processed by the computer. It does not matter whether you are running Linux, MacOS, windows and any other platform. Your CPU is the problem. Want to know more and how to prevent, secure yourself if possible? …
Read More “Spectre & Meltdown Explained”
This week during our HackJam, we will have a presentation by David Wexler from Gripbeats on the product that he and his team is developing here in Hong Kong. The product was inspired by body percussion. A method of creating drum sounds using only your own fingers, hands and body. When properly mastered, a player …
Read More “Maker: Gripbeats – Body Percussion”
On our next HackJam, open & social night, Tuesday the 14th of November 2017, we will have the visit of the team from Origamil Labs. They will be presenting their current product: ORII which is a smart ring that allow you to have phone calls, listen to you messages in total privacy. It will give …
Read More “Presentation from a HK Kickstarter – Origamil Labs”
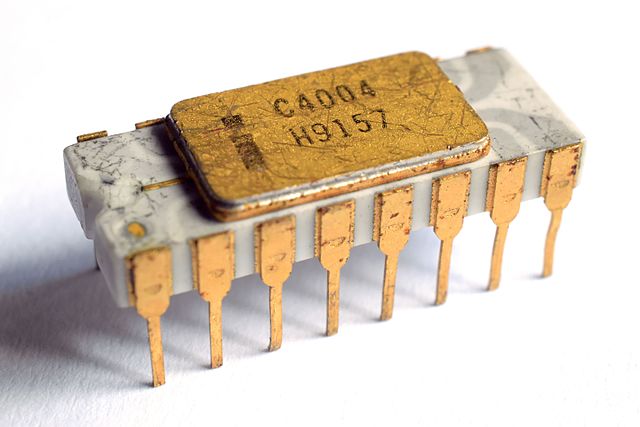
At our next social night – on Tuesday the 31th of October 2017 – we will have a short talk looking at how CPUs work – inside the case and showing some of the key microarchitecture changes over the last 45 years. Come along also to meet people and socialise – we have chilled beverages …
Read More “CPU Architecture overview”
A serious weakness has been found in WPA2, the protocol that most everybody use to protect their Wi-Fi networks at home or at the office. A person in range of your network can exploit these weaknesses to read information on your network traffic that you assumed safely encrypted. The weaknesses can allow that person in …
Read More “Krackattacks explained”
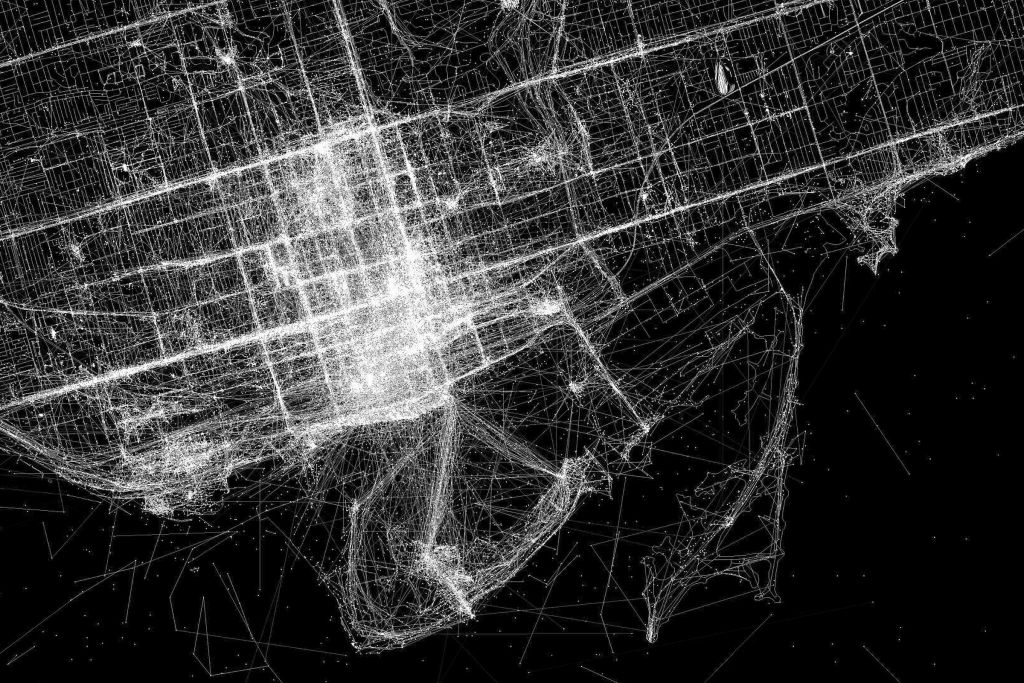
During HackJam this week, we had the visit of Ben from Toronto Mesh. He introduced us the simple and easy way to construct a mesh network based on a network of a few Raspberry Pi2 or Raspberry Pi3. They use the model 2 or 3 from Raspberry Pi because the encryption of the data transfer …
Read More “Mesh Network introduction – CJDNS”
Tonight we had the visit of Karsten Nohl from teh German company: Security Research Labs. He presented his work, some of his latest research on a few security issues with mobile communications. Karsten informed us on the SS7 protocol which is an exchange protocol that all mobile communication providers are using to talk to each …
Read More “Phone Security – HackJam 2016-09-06”